Password Security Best Practices (and Worst!)
November 30, 2023
Every member of an organization is a potential target for today’s cybercriminals. One of the common ways that hackers penetrate an organization’s network and do severe harm is through password cracking.
Although so much awareness has been raised about the prevalence of cybercrime and the importance of creating secure passwords, password cracking remains popular, and effective, for cybercriminals. Understanding the reasons may help you to understand the importance of being proactive about your personal password security.
Why passwords?
One reason password cracking is so popular among cybercriminals is that given the number of passwords that users have today, there is a great temptation to use easy-to-remember, standard passwords to avoid the headache of resetting or even being locked out of accounts. Who can’t relate to having time lost because of doing a password reset, right?
Cybercriminals rely on such human nature and on simple human error to target companies, and passwords are particularly vulnerable to both. Here are some examples…
Reused passwords
In one well-known case, Dropbox was attacked by a hacker. The 2016 breach led to over 60 million user credentials leaked. The cause? An employee who used the same password for both LinkedIn and their Dropbox backend access. It took just one reused password to put the entire company and their huge community of customers at risk.
A more recent example involving PayPal reveals how important good password habits are across the board. In 2023 a hacker used passwords stolen from a third party to attempt to access PayPal accounts. Over 35,000 users had their accounts hacked because reusing their passwords for both accounts.
A 2019 online security survey conducted by Harris Poll and Google found that over two-thirds of individuals reuse passwords for at least two accounts.
Weak or stolen passwords
A 2018 Verizon report found that 81% of hacking-related breaches were successful because of weak or stolen passwords. One well-known case took place when Facebook founder Mark Zuckerberg’s own Facebook account was hacked after his password, ‘dadada’ was guessed.
According to Avato, 90% of employee passwords can be cracked in six hours or less. This statistic is alarming because it illustrates the lengths that hackers will go to violate an account and the number of insecure passwords that members of organizations are using.
Is your password one of these?
The sad truth is that many hackers don’t have to try very hard to access accounts because, despite growing awareness, users routinely employ common and thus weak passwords. Here is a list of the 20 most popular passwords for 2023, are you using any of them?
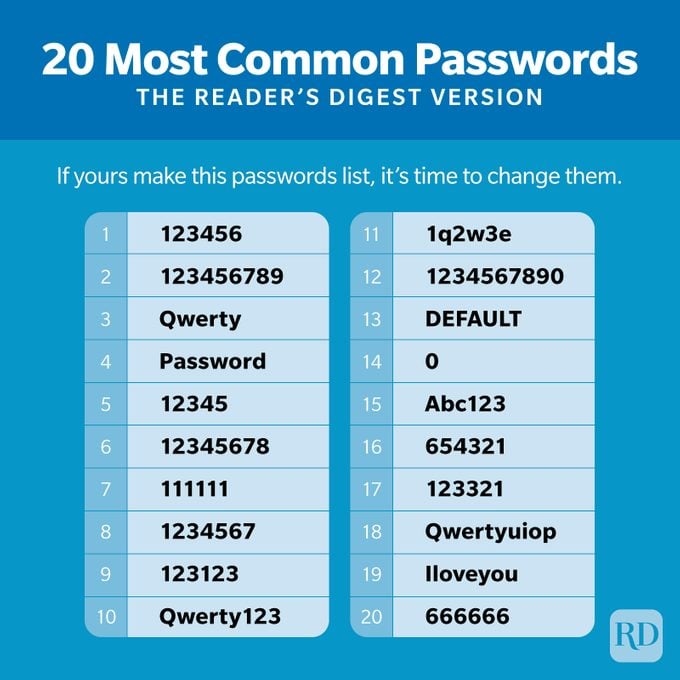
Source: Reader’s Digest
Because this list is widely known, it is an easy place to start for those with malicious intent. Remarkably, there are lists of popular passwords that are as long as 100,000 that hackers can run through an account to attempt access.
Cybersecurity software
Another method that sophisticated cybercriminals may employ is using dictionary software, which allows a hacker to run tens of thousands of real words through a user’s account. Such software may also allow a hacker to run through real word and number combinations.
Phishing
Phishing is a common method of procuring passwords in which a criminal, posing as a trusted source, will contact a user and manipulate them into entering their password through the use of a link. Such emails may warn of security threats or threaten to deactivate an account if action isn’t taken, thus causing a user to let their guard down and enter their credentials.
Not hidden in plain sight
And finally, there are internal threats that should not be overlooked. It is quite common to have sensitive information that is not treated as such be stolen because it is stored in plain sight at an employee’s desk. A sticky note attached to a computer screen is still a common way that passwords are stolen.
There is also the possibility that former employees will access the email accounts of current team members because the passwords have been shared with them in the past.

Password best practices
Sadly, it is often an indifference to the risk and human error that cause so many of today’s attacks. Therefore, the solutions are fairly simple. Want to be part of the solution rather than the problem? Here are a few healthy habits you can develop with your passwords:
The basics
As a rule, you should always select a password that is:
- At least 12 characters long,
- A combination of upper and lowercase letters and,
- Includes special characters and numbers

Add some personal flare
Take the above formula a step further by creating passwords that employ the first letter of each word from the line of a favorite movie or song. For example, “Todo, we’re not in Kanas anymore” could be turned into “twnika” as a starting point. Add part of the name of the movie to make “twnikawz” for extra security. Then, add in numbers and special characters for a hard-to-crack password that is also easy to remember: “twn1ka**wz@!”
Get creative
Another method is using a combination of random, non-connected words as a starting point for a password. “Pinkeggspatchwork,” for instance, would be hard to crack, but easy to remember.
Tools to help
Use a password tool whenever you create or update a password. For instance, Passmeter.com is a free service that will quickly let you know how easy your password is to crack.
No sharing!
Never share your passwords with anyone, no matter how well you know or trust them. There are many different ways that shared passwords become vulnerable once even one other person knows.
No personal information
Never use personal information when creating a password. Your name, your partner’s name, your pet’s name, the year you were born, your social security number, or the town you live in are all popular passwords that are easy to guess and for others to remember.
Switch it up
It is currently recommended that one change the passwords for social media accounts, shared computers, corporate accounts, and email accounts every 180 days.
Don’t reuse
Always use a different password for every account, regardless of whether the account is for personal or professional use.
Storage
And what about storing your passwords? While this can get tricky, there are two rules you should always follow:
- Have you ever received a tiny pop-up message asking if you would like the browser or device to remember your password? You should always select no or disregard this option, no matter how tempting it may be. Likewise, if there are any settings on your browser or device that disable the saving or storing of passwords, you should do so. There is no telling what someone with malicious intent could do if given such easy access to your accounts.
- How will you remember all of your passwords? If you think that you will have trouble remembering everything, the best way to store your information is in a physical location that is locked. Any recording of your passwords should be hard for anyone else to decipher.
Which of the habits and best practices are things that you are currently doing to protect your accounts and your organization? Are there three suggestions that you can implement today in order to feel more secure about not being a weak link in protecting against cybercrime? Remember, we are all potential targets and each member of a team plays an important role in building a strong defense against today’s online criminals.
How managers can help prevent Zoom fatigue
Want more team productivity this year? Try silent meetings (even via Zoom)
<< Back to Blog Posts

